7 Most Effective Methods to Protect Your Business from Ransomware
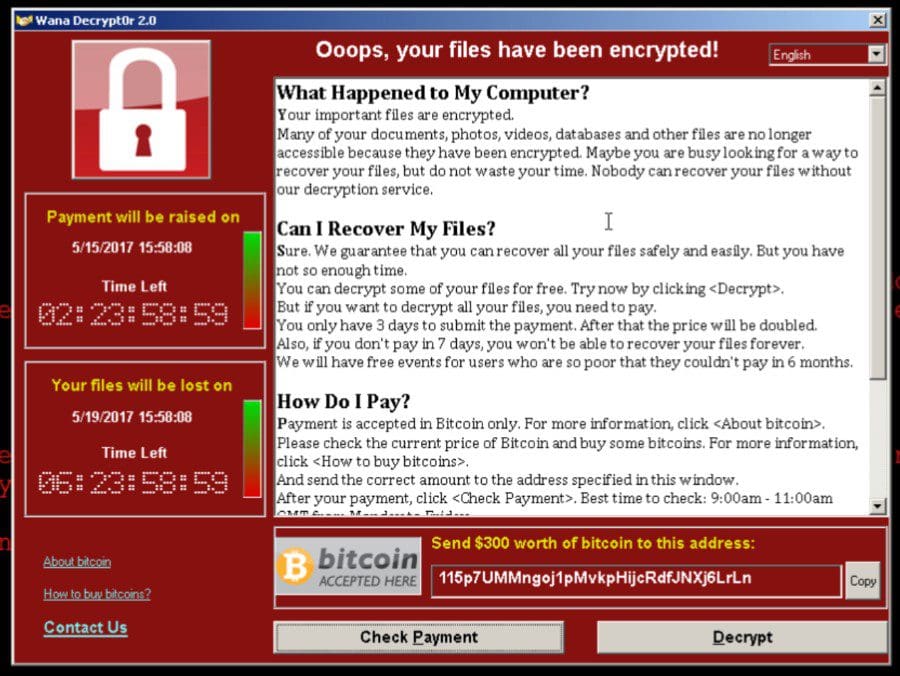
Let us be crystal clear, above antivirus software there is no one solution that is 100% effective in mitigating the risk of ransomware. Some vendors are claiming to have tested hundreds of samples, and that their tool can stop 100% of the samples. We’re sorry, but that is not reality. Why? If any single vendor had a solution that solved the problem completely, the dark business of ransomware would not have grown to be vastly prevalent. The biggest palm-to-forehead moment arrives when light is cast on the fact that a business who just fell victim possessed the tools to prevent it – they just didn’t know how to deploy them effectively.
Bad Guys with Old Tricks
An alarming number of attacks are occurring and just as organizations have begun to trust placing their collaboration applications and data in the cloud, we are reminded that the bad guys are gunning for your data – in the cloud and on premise.
These latest headlines were all generated from the ransomware cyber-attack known as “WannaCry” which has already infected hundreds of thousands of computers globally, but the malware was first detected in March, 2017 and publicly reported stolen from the United States National Security Agency in April, 2017.
This technique isn’t new, hackers have been phishing with email since at least 1996. That means sysadmins have been blocking known attacks and educating their users on why they shouldn’t click certain links or open attachments for twenty years or so. That’s why most organizations have macros blocked, and why the phishing emails provide instructions on how to enable macros so the target can’t have access to the “critical” document that was delivered in the email.
You’re not alone in asking: “Am I protected? What is really going on here? My desktops, servers and file shares are being held for ransom? Can ransomware infect Office 365 files? Would it just be safer to keep all important information out of the cloud? Or, in the cloud? If my business is attacked, how do I recover from this?
We understand that it’s scary but prevention can be simple – here’s a quick list to get you on the right track.
Protect with Prevention: 7 Methods You Can Use Right Now To Combat Ransomware
1. Lock Down Your Backup Targets
It may sound simple but following the 3-2-1 rule from our friends at Veeam is good practice. “According to this rule, 3 copies of the company data should be saved on 2 different media and 1 copy should be offsite.” This article provides further detail: https://www.veeam.com/blog/how-to-protect-against-ransomware-data-loss-and-encryption-trojans.html
The access rights to the Backup Repository Server should be restricted such that only the Veeam service account has access to the Repository Server and the file system.
In case of NAS systems, only the Veeam service account should be provided with the permissions for the Backup Repository.
For security reasons, working on a local desktop with a domain administrator is absolutely not recommended because this can lead to the ransomware spreading around the network very quickly.
Many administrators by default deactivate the Windows Firewall as soon as the installation of Windows is complete. This built-in mechanism can provide protection against ransomware attacks from the network via the Windows security loopholes. It’s considered to be a best practice that you take a little time out and activate the necessary inbound and outbound requirements in the Windows Firewall.
A virus scanner with an activated real-time search should also be installed on all Windows systems. After installing a new server, oftentimes a customer forgets to install their antivirus software. However, since virus scanners access a system deeply, they might block Veeam services and will need to have select ports open.
Are you backing up to shared storage or to a purpose-built dedicated storage array such an Exagrid appliance?
2. Activate a Backup Plan for OneDrive, Teams, SharePoint and Email
Ensuring that you have an active backup plan for OneDrive, Teams, SharePoint and Email has never been more important. With the proper application of a well-built and executed backup solution, you can avoid the issues that are surfaced through a ransomware attack. DocAve Backup and Restore and DocAve Online can help you keep content safe if a ransomware attack hits one of your users or your entire infrastructure. Whether your data lives entirely in the cloud or in a hybrid deployment, DocAve can create a backup plan that ensures content can be segregated and then quickly restored.
Here are a few simple steps suggested by our friends at DocAve, to ensure you are protected:
A. Have a granular backup in place
Ensuring that you have your content backed up at a granular level will allow a quick and simple recovery from a ransomware attack. Once you have quarantined the issue and have clean servers that the content can be restored to, you can carry out a time- or object-based restore of the content that has been lost.
B. Backup your content frequently
Ensuring that you have your content backed up as recently as possible will ensure that any data loss from a full recovery will be minimal. Ensuring that you are following best practices and having multiple tiers of data classification in your backup plans will make this a much easier process.
C. Have a restoration plan in place.
3. Limit End Point Access with Privilege Rights
Application control solutions, endpoint protection products, and even least privilege solutions from our friends at BeyondTrust have various degrees of success in mitigating ransomware but none are 100% effective. Why? Modern ransomware does not care about privileges, does not always launch separate executables, and sometimes targets obscure devices.
The delivery of the payload is equally as impressive to identify. It can come from an exploitable vulnerability, an errant executable (the easiest to stop), PowerShell script, or embedded as a macro or script in a file or website. What makes this a little more disturbing is that many attacks combine methods and use a command control server to hold encryption certificates verses locally based per infection that can be cured with a vaccine.
Based on these facts, therefore ransomware is so difficult to stop and no one technology – from any vendor can 100% predict the next exploit before it happens and this cannot be 100% effective which is why it is truly why you must do your due diligence as much as you can.
There are some actions you can perform with products like PowerBroker for Windows from Beyond trust to minimize the threat. Unfortunately, nothing will ever replace training users to not click on phishing links or select “Run Macros” when opening an unknown file. However, we can reduce their rights and with a few rules that are easy to implement, block the vast majority of mistakes users can make, stop droppers from executing, and block vulnerable applications from being leveraged against your assets.
4. Continuously Provide Training to Users
Again, it’s a simple but effective method when it’s baked into a company’s procedures. Educating users on the practice of phishing links and running macros goes a long way. Make training part of your onboarding process and revisit it every year – and depending on the size of your organization, perhaps even once a quarter!
5. Control Internet Access
“WannaCry” worked so well due to improper security at the perimeter. This lack of security lead to the attack not being detected and controlled as most places do not control outbound internet access; meaning everything is accessible without any protection.
If you use URL filtering, packet inspection, geo IP blocking etc., and detect applications making a call out to a command and control server, or other malware type activities, you can restrict access heading externally to the internet. These protects also allow for a company to handle data exfiltration which helps secure their intellectual property.
An example would be to limit access from only desktops and users with an account either at the firewall or using a proxy server, all other access including direct access is denied. Then layer on filtering with inspection and analysis of the traffic with only specific applications like web browsing and SSL. All other traffic that is business related would need exceptions.
Typical port based firewalls can be configured to allow tcp/80 and tcp/443 out from defined networks or devices, however inspection of the traffic is not available on all vendor products.
6. Keep Up with Patches and Blocks
Keeping up with recent patches (Intune or SCCM) would have stopped the recent “WannaCry” from attacking a system. Our friends at Palo Alto had a block for this about a month ago. Patching and blocking is one of the most cost-effective actions a business can take. Also, Microsoft recently published a technical guide for customers in the wake of all that is happened. You can find it here. There is a brute-force method you can implement as well, called a software restriction policy. Implemented via GPO (Group Policy Objects), it can prevent unknown web applications from running on your computers before they start. While this method is a bit more work, please don’t hesitate to ask us how to initiate it. However, simply implementing the right tools and establishing proactive maintenance is the best way to provide protection and avoid costly mistakes.
7. Seek Outside Consulting Advice
An attack on your business can have severe and detrimental consequences. With so many tools on the market, an independent consulting company like SkyTerra can help you quickly navigate and find the right-sized solutions for your business, saving you time and resources. Don’t wait to take preventive steps and fall victim. Protect your company today – contact us or call 1-603-769-3172.
