How to Replace Microsoft Office 365 Activity Alerts on Global Full Control Accounts using Azure Log Analytics
As a managed service provider, SkyTerra stays on top of application changes and the cyber security landscape so our clients don’t have to. Microsoft’s deprecation of Office 365 Activity Alerts is one such issue. To create alerts that will protect your cloud data, use Azure log analytics to enable global full account controls.
The Issue: Office 365 Alerts Are Going Away
With most cloud platforms, there is a global full control account deployed that has 100 percent access, or an “in case of emergency, break glass,” with GOD rights. Most companies rely on activity alerts to manage access to these accounts, but what happens if someone unauthorized gets access to this account?
Recently Microsoft announced they are removing activity alerts in Office 365 and replacing them with alert policies. Both the activity alerts and the alert policies can take anywhere from 30 minutes to an hour to fire off the alert. By that time, most hackers have already either gotten the information they need or have planted enough backdoors and trojans to get in later.
Solution : Set Up Alerts for Global Full Account Access Accounts
Using Microsoft’s Azure Log Analytics KQL script and a simple consumption logic app, we can monitor any global full control accounts or monitor any high-level account login that the hackers may try to use.
The solution uses the following Microsoft KQL query and a simple Azure logic app to monitor, alert and email the break-in in less than 6 minutes. This gives us enough time to STOP the attack before damage can be done.
System Requirements
- Make sure you deploy Azure Log analytics to your Azure subscription (in the correct region).
- Add the Microsoft 365 data collector to your log analytics.
- Create a resource group to contain the logic app.
- Deploy the logic app as a consumption-based app (also in the same region).
How to Create the Azure Logic App
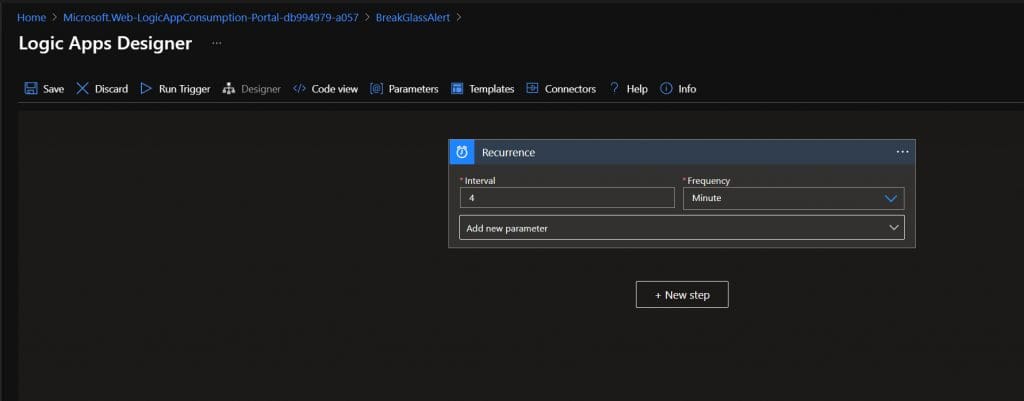
Step 1. Recurrence: Let it run every 4 minutes.
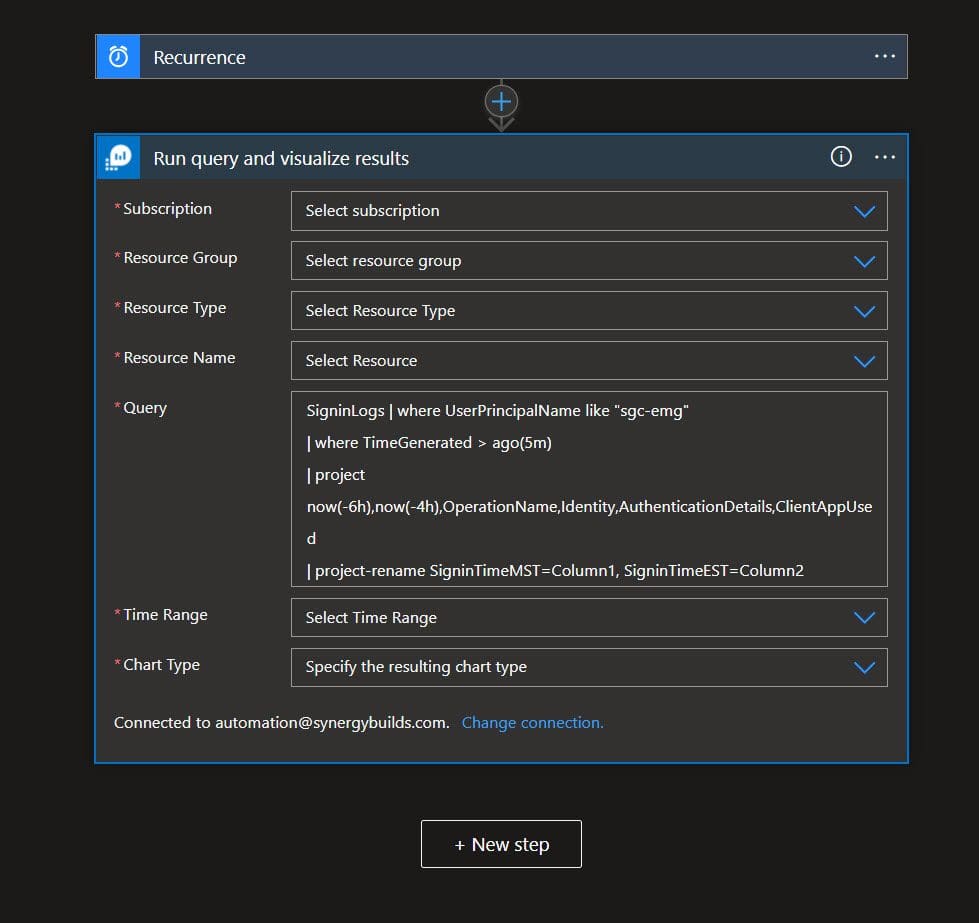
Step 2. Use the Log Analytics, Azure Monitor Logs: Run query and visualize results.
You will need to log into your subscription, select your tenant, log analytics space and insert the following KQL in the “Query” field. Make sure to select “HTML” as the output in the “Chart Type” field.
Kusto Script: (Note: In my script I am getting both the EST and MST time.)
SigninLogs | where UserPrincipalName like “Your breakglass account name”
| where TimeGenerated > ago(5m)
| project now(-6h),now(-4h),OperationName,Identity,AuthenticationDetails,ClientAppUsed
| project-rename SigninTimeMST=Column1, SigninTimeEST=Column2
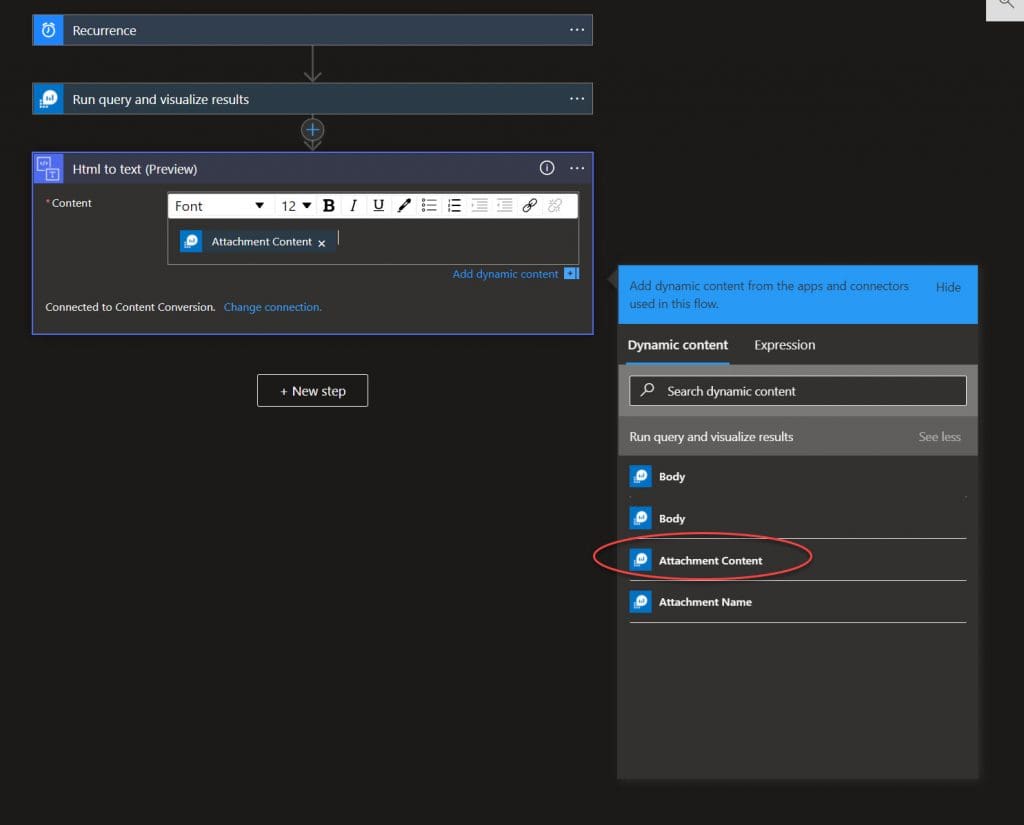
Step 3. Use the “HTML to Text” Connector: Insert the “Attachment Content” into the converter.
Step 4. Add In Our Condition: Tell it to give us a result if the text contains “sign-in activity.”
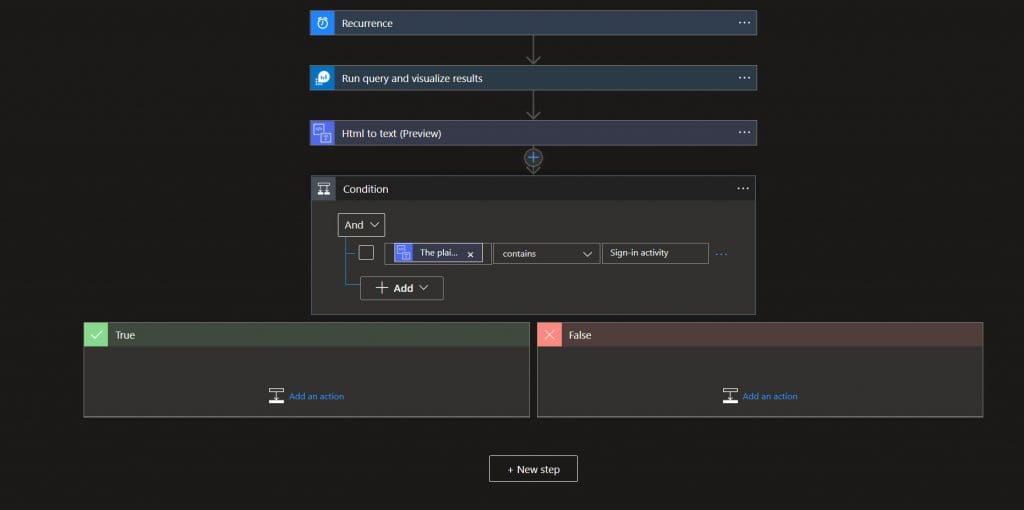
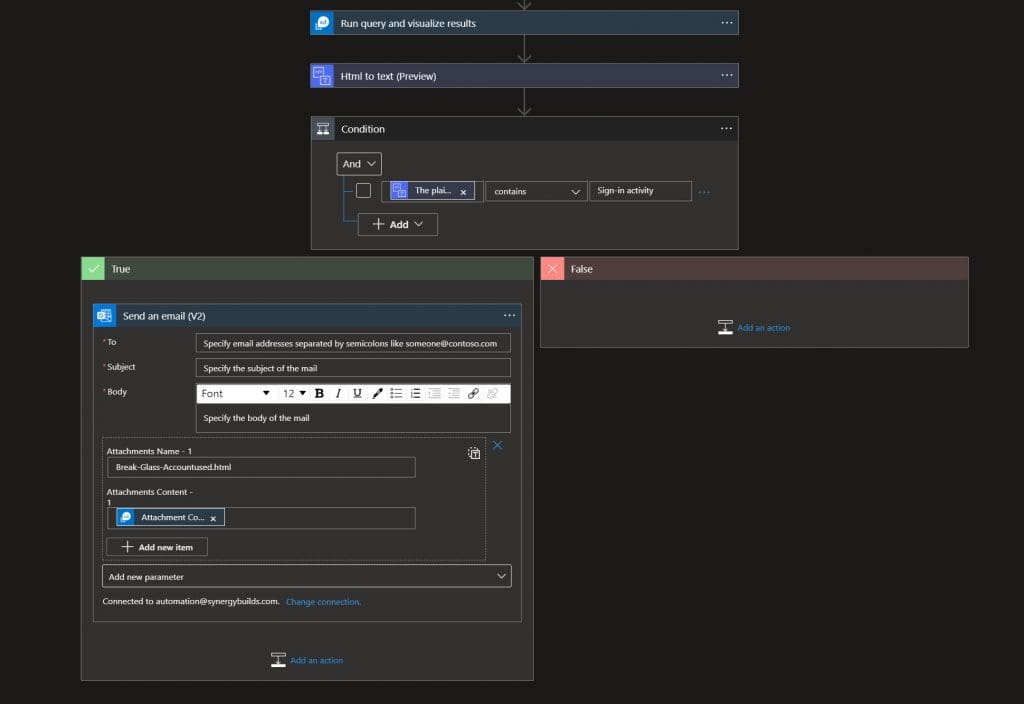
Step 5. Add “Outlook Email v2”: Send an Email, when our query returns a true response.
Make sure to add the “Attachments” parameter to the email template.
You will need:
- Mail to: Use your security Group or Security team email
- Subject: We suggest using “Break-glass Account Used”
- Attachment Name: We suggest using “Break-glassAccountuse.html” but whatever you choose, make sure the attachment name ends in .html
- Attachment: Use the “attachment content” from the Dynamic Content list
Now, run our trigger and see a false output, as the account has not been used in the last 4 minutes.
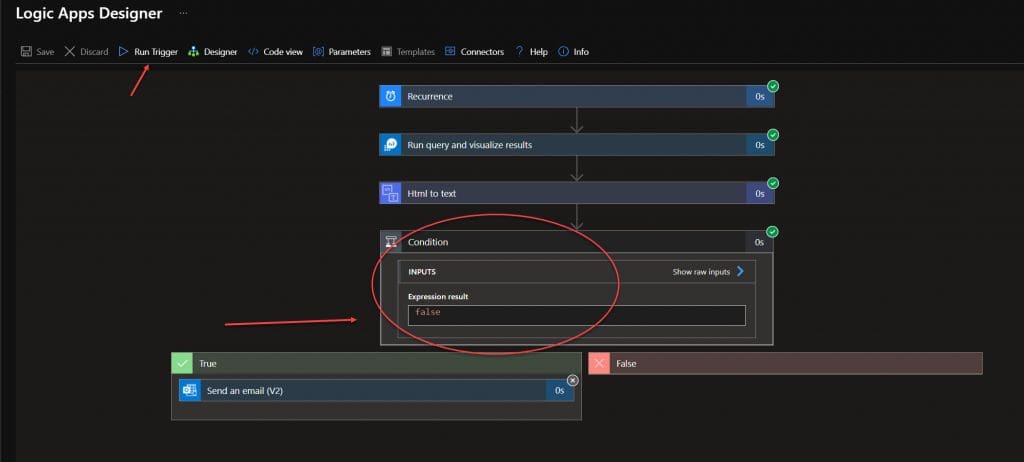
Step 6. Test
Log in with the account you are monitoring from a separate browser (Google incognito) and then wait for the email to arrive.
Full Logic App Example:
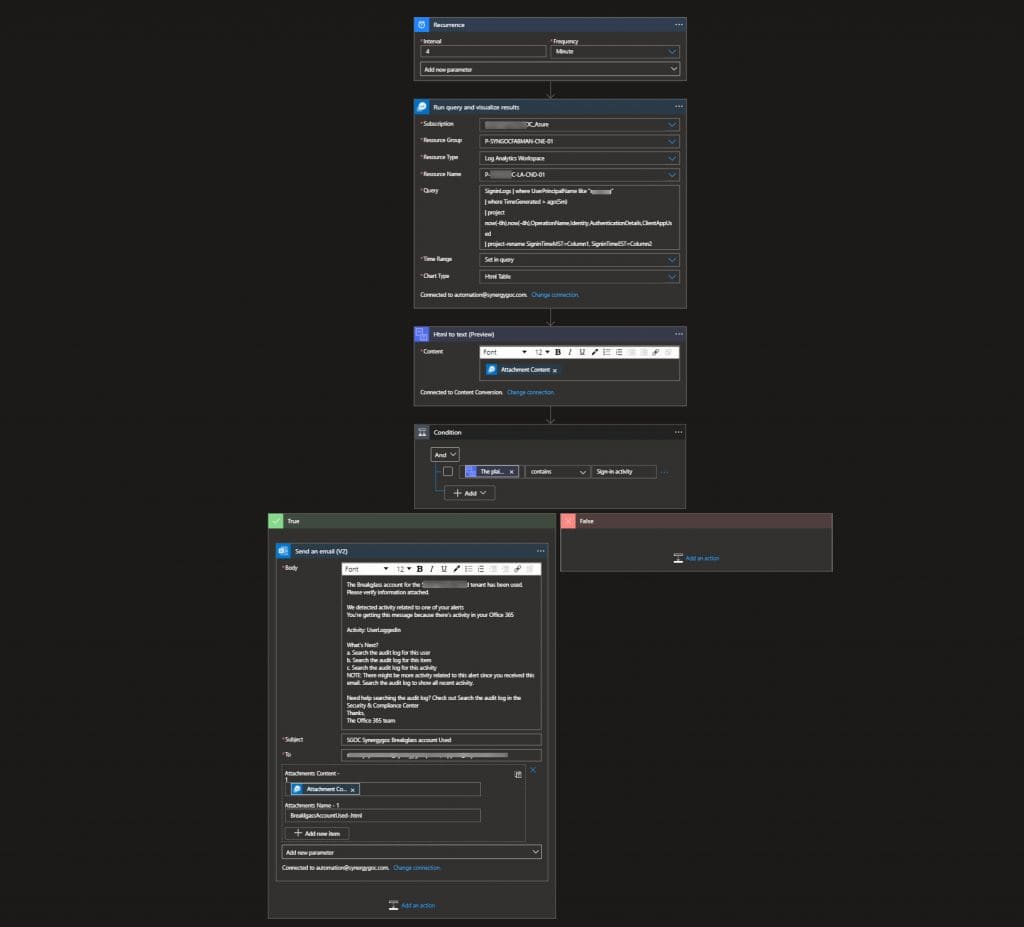
By following this Microsoft KQL query and a simple Azure Logic app, you can create alerts for global full control accounts in real time. With this implemented, anytime an unauthorized user accesses your account, you can quickly stop their access by going to Azure Active Directory and block the user login.
Of course, you could also reach out to SkyTerra for IT support to take tech issues off your plate. For our managed services and cyber security clients, we take care of issues like this for you proactively. Contact us or book a meeting to learn more.
